IAM – manage users and permissions better
Flexible modules and functions that take you further.Modular IAM solution delivers best-in-class performance for web application users
Read the story of how Login-Master started. It will help you better understand our modular B2B solution for access and identity management. We developed it from partly existing components in 2016. Why? To fulfill the basic requirements of a web portal project.
End users of the unique software construction kit are not only business customers, clients, partners or suppliers, but also members of an alliance. In regulated areas, such as government institutions, health care, insurance companies or banks, Login-Master fits perfectly into the existing system landscape. And for the users of a portal, Login-Master offers authentication and access rights control made to measure.
Successful: IAM modules combined with an open-source SSO system
To implement it, we had a choice between two open-source offerings: ForgeRock, one of the oldest platforms for CIAM needs, or the newer “IAM rocket” Keycloak with no licensing costs. We chose Keycloak.
Keycloak is our SSO for web applications
In it, we found one of the best open-source SSO solutions. Because Keycloak delivers authentication as the most requested IAM function. And it works perfectly even when the number of user accounts, as well as their access permissions, is low. Our customer challenge:
The web portal managed more than a million users.
Developed for increasing market demand: the user lifecycle for all identities
An important part was missing besides the login functionalities – the user lifecycle management. For this reason, we combined access management with all the necessary identity functions. And formed a holistic CIAM solution. For B2B tasks, we added intelligent modules, e.g. to map complex roles and authorisations.
This makes Login-Master one of the smartest innovations. Because it combines the most advanced SSO software with flexible access and identity modules. In addition, a sophisticated user lifecycle that offers process automation. With delegated administration, workflows, auditing and much more. This guarantees fast, controlled access to sensitive, protected information. The modules contain automated, highly reliable functions thanks to the strong Java backend engine iDOME. The company intension developed this framework to make it easier for developers to script and automate IAM workflows. Small companies, medium-sized businesses and large enterprises such as Deutsche Telekom use iDOME.
Our modular solution helps extend IAM functionality for B2B according to customer needs:
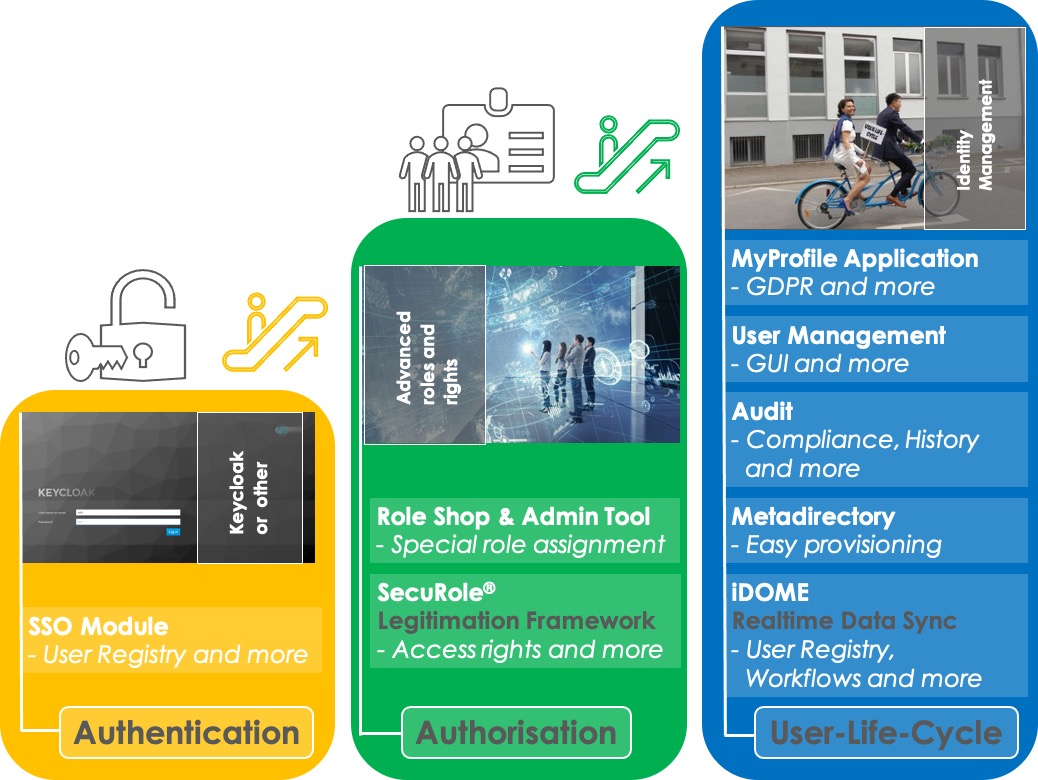
The illustrations below will help you better understand our IAM solution. It consists of three parts:
Authentification
Everything you need for logging users into protected Internet applications.
Whether Single-Sign-On or Single-Sign-Out.
With an Identity Broker or various identity providers.
Self-service and privacy implementation are included.
Authorisation
Add SecuRole® to manage access rights via token-based authorisations.
Incredibly fast and very secure.
It helps you overcome some digital hurdles, such as setting up cloud access for different user groups.
User lifecycle
This is your workhorse for the digital management of your user identities.
The Identity Suite manages them properly according to the GDPR regulation.
Fast and automated – thanks to the workflow engine.
Comprehensible and retrievable due to event storage.
With audit functions and mail engines for recurring processes.
All the above modules massively alleviate the work of your administrators and support.
Modularly combinable B2B functions automate and relieve support staff
In addition, there are very useful business functions. Our role shop allows users to control activities and permissions themselves or request them using automated workflows. And the admin tool offers the same added value: relieving burden on support. This is how companies seamlessly design their e-business with different parties. No matter if partner or supplier – the delegated admin function takes care of external identity changes.
All functions in one software – these components make the difference:
Java developers, government institutions or companies of any size and any industry rely on the Red Hat open source project, which is now part of IBM. If you are looking for a Keycloak consultancy, then start with our experts.
Keycloak is not your favorite? That doesn’t matter at all, because we also integrate other SSO solutions for you. How about Okta or ForgeRock?
Authorisation control:
For this, there is the framework for authorisation: SecuRole®. It is new, but already proven. It addresses the current complexity of access rights and their fluctuation in the Internet.
SecuRole® opens up new paths to unimagined possibilities, especially for B2B web portals and cloud access. This technology eliminates the need for complicated administration via group memberships. Because token-based authorisations coordinate access rights and roles digitally. This eliminates the need for time-consuming provisioning. Read more about the smart network here.
Intuitive: Self-service roles and permissions for web application users
In addition, users can easily request additional roles for themselves and others. With automated logic, the role store enables quick selection and assignment of authorisations. And all this with fully automated support. In addition, the system securely locks outgoing web portal members. This is especially important for delegated administrators. Whether basic user or local admin: different permissions, different functions of multiple, legally separate parties in a cloud environment can be mapped. This also eliminates the security risk.
Find the right starting position for the future: This is the modern way to manage authorisations and associated processes.
Identity management:
Identity Suite or user lifecycle management relies on the long time-tested framework iDOME. You want to understand why it would be better to rely on a central identity management?
It is still common for an application itself to manage its users. This is insecure and inefficient. Integrating and maintaining a homegrown IAM part costs you a huge amount of time. Every additional new application you include requires further development. It brings more complexity and further incompatibilities with the GDPR regulation.
Overcome all hurdles to more business with modular IAM building blocks
Authenticating a user is the first step in complete identity management. You’re headed in the right direction. Take your application to the next level. Extend your isolated access solution. Why? To manage a large number of accounts and permissions. To be faster and better. Address complex authorisations within your applications or multi-dimensional access to your Internet portals – even in the cloud.
Our modular identity management takes you to the next level.
And the right management of users immediately relieves your support. It saves you a lot of time and money. Authorising an identified user is the final step towards a functioning system – important for security, efficiency and user satisfaction.
High user numbers or complex B2B authorisation structures are no longer hurdles for you. Because as a provider of an Internet application, you need answers to the many technical challenges. And you want to keep costs as low as possible. These days, you can choose comprehensive, ready-made services from the cloud to do just that. But not every application is made to tap this enormous potential. In response to this dilemma, we designed Login-Master: A modular access and user management solution that has everything you need to run your legacy applications in the cloud in the future.
Managing your web portal users, especially in the cloud will no longer give you sleepless nights:
-
- Faster through digitisation, centralisation and automation with hardworking helpers
- Increased security for your users through open source, GDPR compliance and intelligent modules, adapted to your individual needs
- More confidence by working with IT security experts and using their best solutions
- Full freedom to concentrate on the actual core business
Curious which parts of Login-Master will add the most value?